As a system administrator, you know that having control over the local Administrators group on domain joined PCs is critical for maintaining security. Luckily, you can establish this control by using Group Policy Preferences.
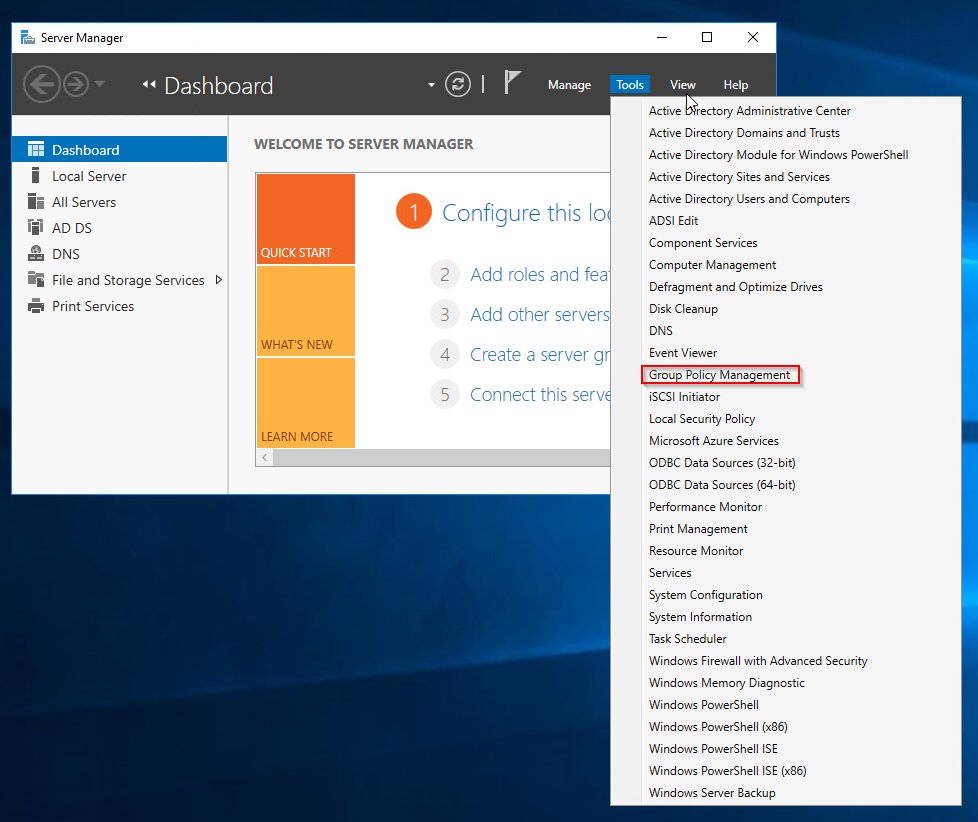
Open Server Manager and click Tools> Group Policy Management.
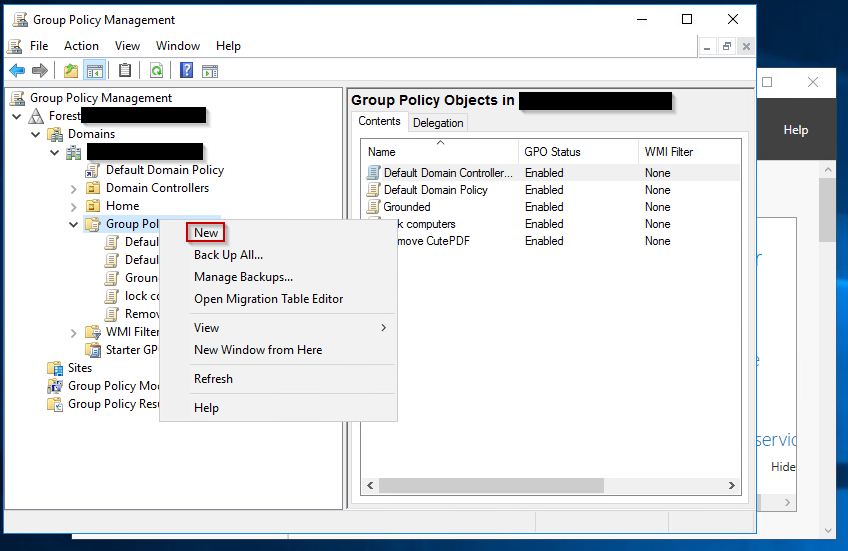
Right click on Group Policy Objects and click New.
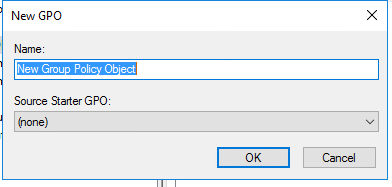
Give it a name like Restrict admin access and click on.
Highlight your new GPO and click Action > Edit.
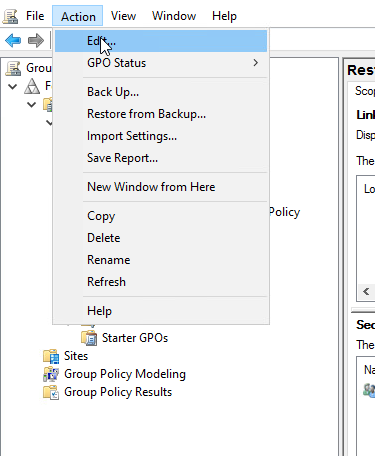
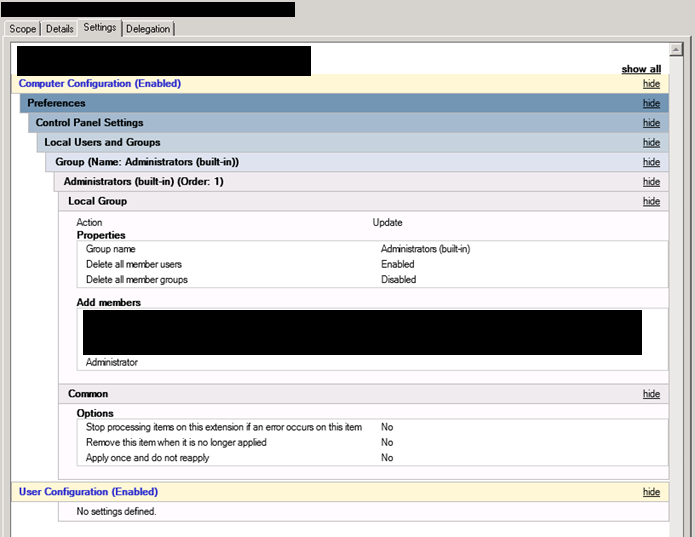
To configure this policy, go to Computer Configuration > Preferences > Control Panel Settings > Right click on Local Users and Groups and Select New > Local Group. Now hit OK.
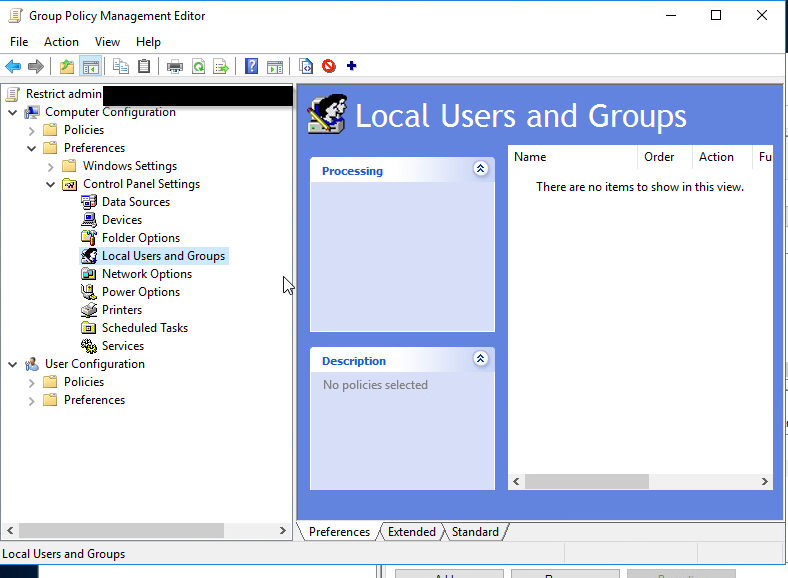
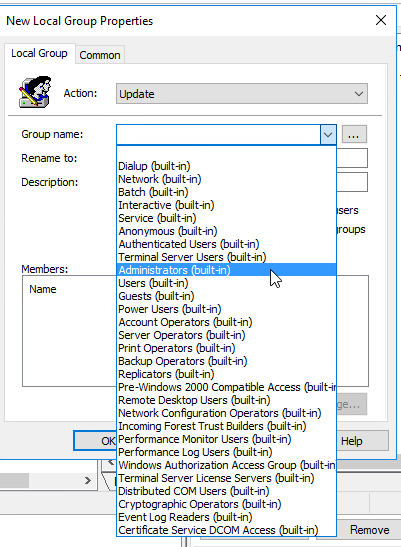
In the Group Name Field there is a drop down, choose the “Administrators (built-in)” group. Check the box that says Delete all member users. Click the add button. Add Domain Admins and any other users or groups you would like to still be an admin. WARNING: it is imperative that correctly configure these members or you can lose admin access to anything this is applied to.
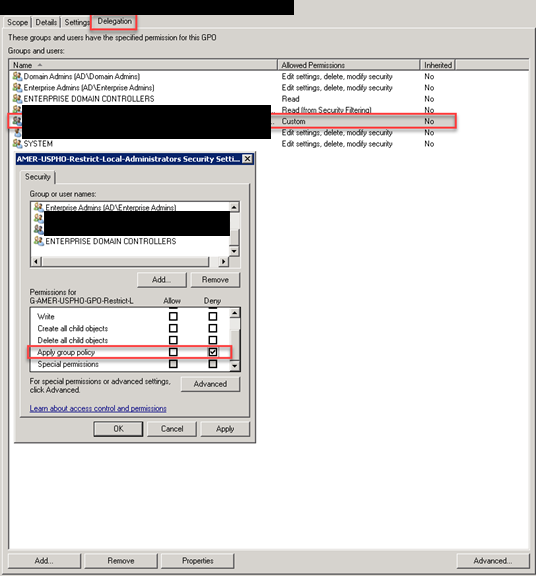
Next we go back to our GPO and click Delegation at the bottom click Add. Now add your freshly made security group and click OK.
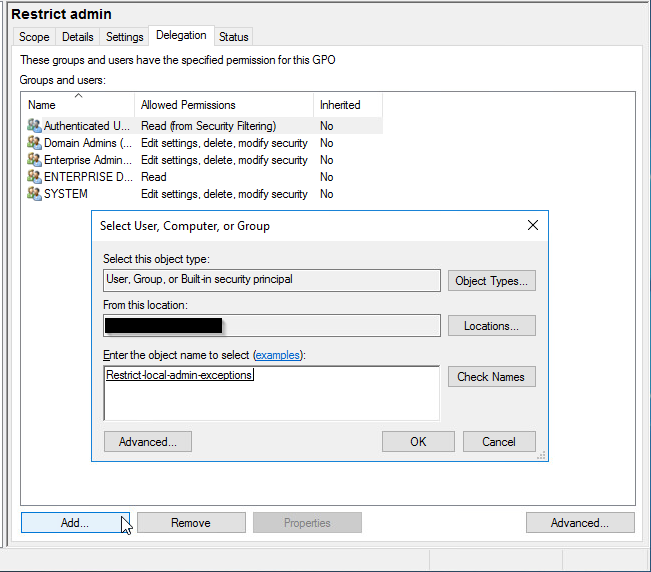
In the next window, click OK don’t worry about the settings yet, we are going to change the permissions in the next step.
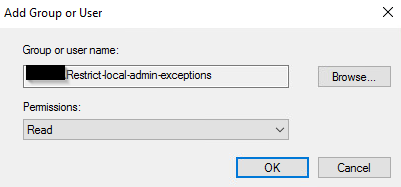
Next we are going to edit the permissions click on the security group then click Advanced in the bottom right corner.
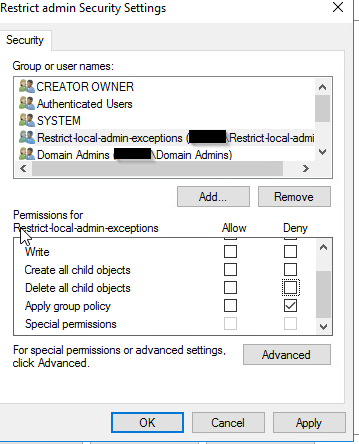
Now click on our security group we made, and click deny under Apply group policy. This is the only thing you want to Deny. Click OK. You are now done creating the GPO.
Once the GPO is linked, all users (and potentially all groups) not specified in the policy will be removed from the “Administrators (built-in)” group on any computer to which the policy is applied.
Exceptions to the policy can be made, such as allowing an AD account to remain in the “Administrators (built-in)” group or creating an account local to that computer. To do this, prevent the application of the Group Policy to that computer by placing the computer object into a security group for such exceptions. This will deny the ability to apply the settings contained in the Group Policy to that computer.
Managing exceptions then becomes an exercise in simply adding or removing computers from the security group set up to hold the machines where an exception is desired and then using GPUPDATE or allowing the GPOs to refresh.
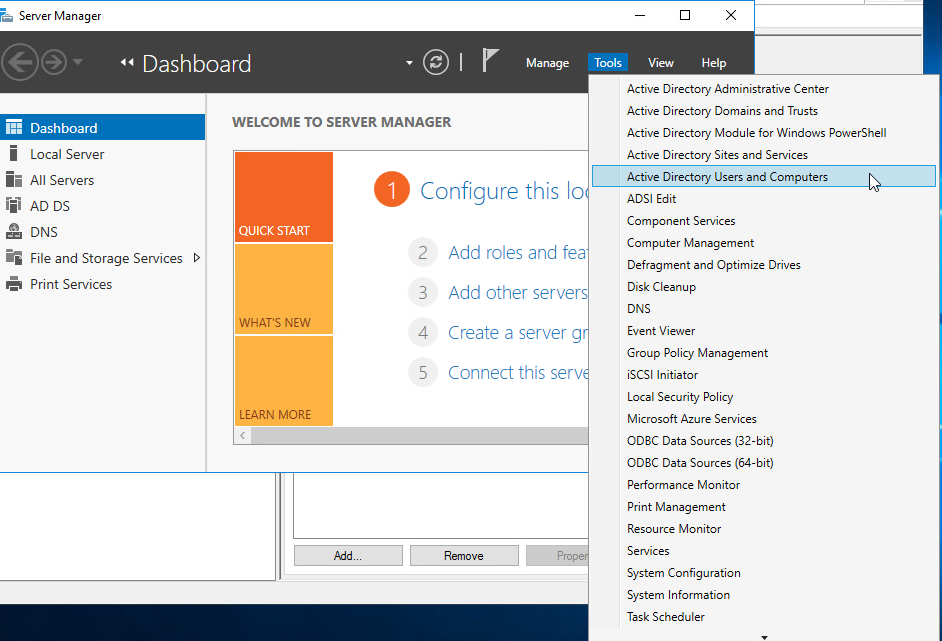
Create a security group for exceptions. Open Server Manager and click Tools > Active Directory Users and Computers.
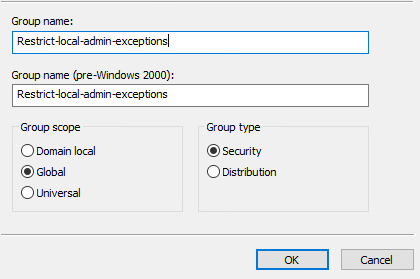
In the navigation pane select the contain in which you want to store the group. For the name of the group you should refer to this as the Admin Exceptions. For the description, Computers in this group will not receive the GPO that removes admin accounts. In the Group scope the selection depends on your Active Directory forest structure. If all of the members are from the same domain, then use Global. In the group type section, click security, then click OK.
It’s important to note that exceptions are applied upon the computer object, not on the user object for the user being granted an exception.
The net effect is that this becomes, in essence, a “Deny All” type approach. Member AD and local accounts not listed in the policy will be stripped from the group each time the policy is applied, unless the computer is a member of the “exceptions” security group. This allows for a standardized and somewhat “set and forget” model for enforcement on computers where no exception is required.
Enforcement Strategy/Plan
While the initial setup of the Group Policy objects and “exceptions” security group might take some effort, once configured it will require little in the way of maintenance.
Auditing and Monitoring
While the Group Policy method of restricting membership in the local “Administrators (built-in)” group offers no immediate auditing or monitoring abilities, there are ways to create those mechanisms via native tools such as PowerShell or potentially use tools such as Alert Logic to provide those capabilities.
For example, since exceptions are granted based upon membership in a security group, it would be possible to dump a list of the members of these groups and compare them against a list of machines where an exception has been granted. Similarly, reports can be run against machines where exceptions have been permitted to ensure that only the authorized accounts have been added to the “Administrators (built-in)” group.
Thank you for reading and if you have any questions please comment below.